
Security bod Maarten van Dantzig says a large number
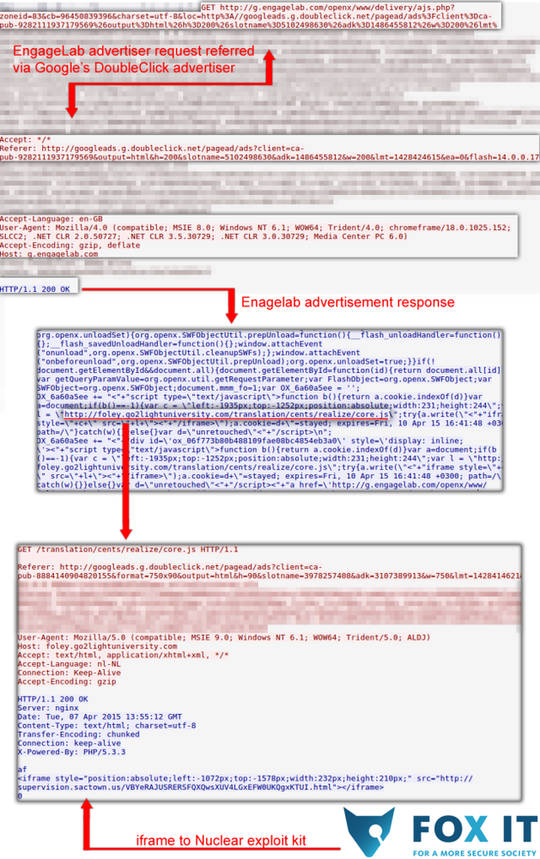
of Google ads sold through Bulgarian reseller EngageLab have been
pointing users to the dangerous Nuclear exploit kit.
The Fox-IT binary basher found the campaign, which may at the time of writing have been subject to the Choc Factory's boot, could result in a "very large" number of attacks.
Victims could be compromised over Adobe Flash, Java, and Microsoft's lonely orphan Silverlight.
Nuclear exploit kit redirection was first observed overnight targeting Fox-IT customers, van Dantzig says.
"The Fox-IT SOC (security operations centre) has detected a relatively large amount of infections and infection attempts from this exploit kit among our customers [and] we suspect that this malvertising campaign will be of a very large scale," van Dantzig says.
"Though we have not received any official confirmation, we are currently no longer observing malicious redirects from the advertisement reseller."
Van Dantzig reported the command and control server and three others foisting the exploit kit to Google.
He recommends users block access to '85.143.217.196', deploy an advertisement blocker and update (or uninstall) Flash, Java, or Silverlight. ®
The Fox-IT binary basher found the campaign, which may at the time of writing have been subject to the Choc Factory's boot, could result in a "very large" number of attacks.
Victims could be compromised over Adobe Flash, Java, and Microsoft's lonely orphan Silverlight.
Nuclear exploit kit redirection was first observed overnight targeting Fox-IT customers, van Dantzig says.
"The Fox-IT SOC (security operations centre) has detected a relatively large amount of infections and infection attempts from this exploit kit among our customers [and] we suspect that this malvertising campaign will be of a very large scale," van Dantzig says.
"Though we have not received any official confirmation, we are currently no longer observing malicious redirects from the advertisement reseller."
Van Dantzig reported the command and control server and three others foisting the exploit kit to Google.
He recommends users block access to '85.143.217.196', deploy an advertisement blocker and update (or uninstall) Flash, Java, or Silverlight. ®

No comments:
Post a Comment